OSINT Blog
Browser Extensions for OSINT Investigation
Browser Add-ons can be of great help to OSINT investigators in simplifying and automating tasks. We’ve collated a list of some of the browser add-ons that the Skopenow’s team uses most frequently during internet investigations.
Continue ReadingLeveraging OSINT for Corporate Security
To successfully protect people and assets, corporations must contend with several crime types, including theft of property, money, and data, intellectual property breaches, fraud, and cyber-attacks.
Continue ReadingThe Lego Method: An Investigator's Process for Enhancing OSINT
My bewildered colleague, who wanted to observe a digital investigation, struggled to comprehend my focus on the Facebook profile of a seemingly unimportant woman. I found her by reversing the phone number of a current tenant living where the subject allegedly resided. However, no obvious links between the two individuals existed: major age gap,…
Continue ReadingGoogle Dorks for OSINT Investigations
Dorking is a technique that uses advanced search operators within Google Search and other search engines to find information. Primarily used to locate security holes in the configuration and computer code within websites, Dorks can also provide investigators with opportunities to enhance intelligence gathering during OSINT investigations.
Continue ReadingCrime Scripts: Interpreting Criminal Decision-Making to Disrupt Crime
To prevent and disrupt crime and disorder at scale, investigators are increasingly utilizing scientific approaches. Problem-oriented policing (POP) is an approach that involves using analytics to identify and understand a specific problem and develop a tailored response.
Continue ReadingCryptocurrencies: The Evolution of Criminal Funds
In the absence of effective regulation, the criminal use of cryptocurrency is accelerating. Whilst the scale of the criminal use of cryptocurrencies is difficult to determine, it was estimated to be roughly $14 billion worth of transactions in 2021. $14 billion represents only a small share of the overall cryptocurrency market, however, this figure…
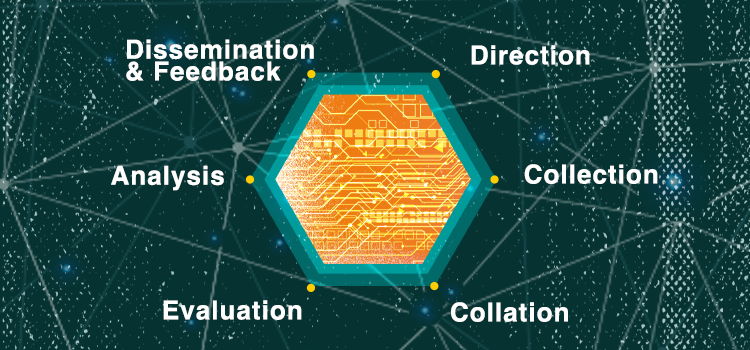
Continue ReadingThe Intelligence Cycle: Generating OSINT from OSINF
The Intelligence Cycle is a structured process that outlines the steps involved in producing intelligence. Intelligence, most simply defined as information with added value, is the output of the intelligence cycle, where raw data and information flow into the process and emerge with value for the organization.
Continue ReadingBusiness Due Diligence: Understanding the Fake Agency Fraud Behind Madbird.
In 2020, the world went into lockdown. During this time, many people lost their jobs and many others began to work from home full-time. During this time, Madbird, a London-based digital design agency, hired roughly 50 remote employees worldwide for management, sales, and design positions. Job ads were posted internationally, promising sponsorship to…
Continue ReadingHow Government Agencies Utilize OSINT
Intelligence-led government operations utilize reliable, relevant, timely, and actionable intelligence from the internet. OSINT enables government agencies to collect and analyze information from the internet relating to their criminal investigations, infrastructure and action planning, and tackling misinformation.
Continue ReadingMoney Mules: How Organized Crime Groups Recruit Via Social Media For Money Laundering
When criminals profit from crime, they need to make their money look legitimate. Criminals avoid using their bank accounts to transfer their criminal funds directly as this would easily link them to their criminality. The criminals first want to move the money around to create a complicated trial. To do this, they launder the money, moving it around…
Continue Reading